What is a CTF competition?
- Capture the Flag (CTF) is a special kind of information security competitions. There are three common types of CTFs: Jeopardy, Attack-Defence and mixed. Jeopardy-style CTFs has a couple of questions (tasks) in range of categories. For example, Web, Forensic, Crypto, Binary or something else.
What is CTF Cyber Security?
- Capture The Flags, or CTFs, are a kind of computer security competition. Teams of competitors (or just individuals) are pitted against each other in a test of computer security skill. Very often CTFs are the beginning of one's cyber security career due to their team building nature and competetive aspect.
What skills do you need for CTF?
- Playing capture the flag (CTF) competitions might need some basic prerequisite skills. You will need to have some basic knowledge of networking like subnetting, TCP/IP, routing and similar. Also, it is important to know some linux commands which will help you in using command line tools on kali linux.
What happens in CTF?
- CTF (Capture The Flag) is a kind of information security competition that challenges contestants to solve a variety of tasks ranging from a scavenger hunt on wikipedia to basic programming exercises, to hacking your way into a server to steal data. ... This goal is called the flag, hence the name!
How do you know if cyber security is for you?
- You're a digital native.
- You're good at identifying what could go wrong.
- You're realistic.
- You've got an eye for detail.
- You're curious.
- You like new challenges.
- You're methodical.
- You're a strong communicator.
Is coding required for cyber security?
- Entry-level cybersecurity jobs don't necessarily require coding ability. ... Python is great for automating scripts that make your role as a cybersecurity professional more efficient. C and C++ are two of the most powerful programming languages, more so than Python or JavaScript.
Does cybersecurity pay well?
- According to CIO, cyber security professionals earn an average of $116,000 annually or $55.77 per hour, for instance, while PayScale estimates that the average salary for computer security specialists is around $74,000, with location as a major factor in pay structure.
Networking:
- Explore the world of data communication.
- Learn about various protocols and techniques used to transfer different varieties of data throughout a network
Forensics:
- Look for hints and pay attention to detail.
- Find the hidden secrets behind a benign document.
Cryptography:
- Learn the art of securing data from prying eyes and breaking the defenses of encryption
Reverse Engineering:
- Break things into pieces, understand how they work, and apply the learnings to attack and defend.
Quiz:
- Know the various exploits, tools and news in the security industry.
Treasure Hunt:
- Use and learn your open-source intelligence skills from here.
- CTF idea created and developed by BYITC team under the guidance of Dhruv Maheshwari.
Certification
- there are 40 intriguing topics to inspire the technologist in your kid. Along with the course, your kid will have access to various references to get even more information, if one is interested. The course also includes an assessment to gauge your understanding of the topics. All the topic contains 20 questions for the test. Kids answer these questions with the help of Google.
Passing Score
- you may score above 70% or 80% on certification and CTF Lab as well to achieve the minimum passing score.
Time duration
- Once you enroll you need to finish certification and lab both within 4 weeks.
- backbase
- siMpliDi5
- xehed it!
- frenchmen
- nooby caesar
- number game
- Dr. Octopus
- base wars - lv1
- Base wars - lv2
- Base wars - lv3
- Missing eyes
- Double trouble
- Double trouble - 2
- math issues
- World threat
- Mobinary
- h3xy_h1tl3r
- you cant see the flag
- Hexicat
- Hiding in plainsight
- b0r3st
- Toy Poodle
- Ali3n1fi3d
- op_zero_walk
- geolocator
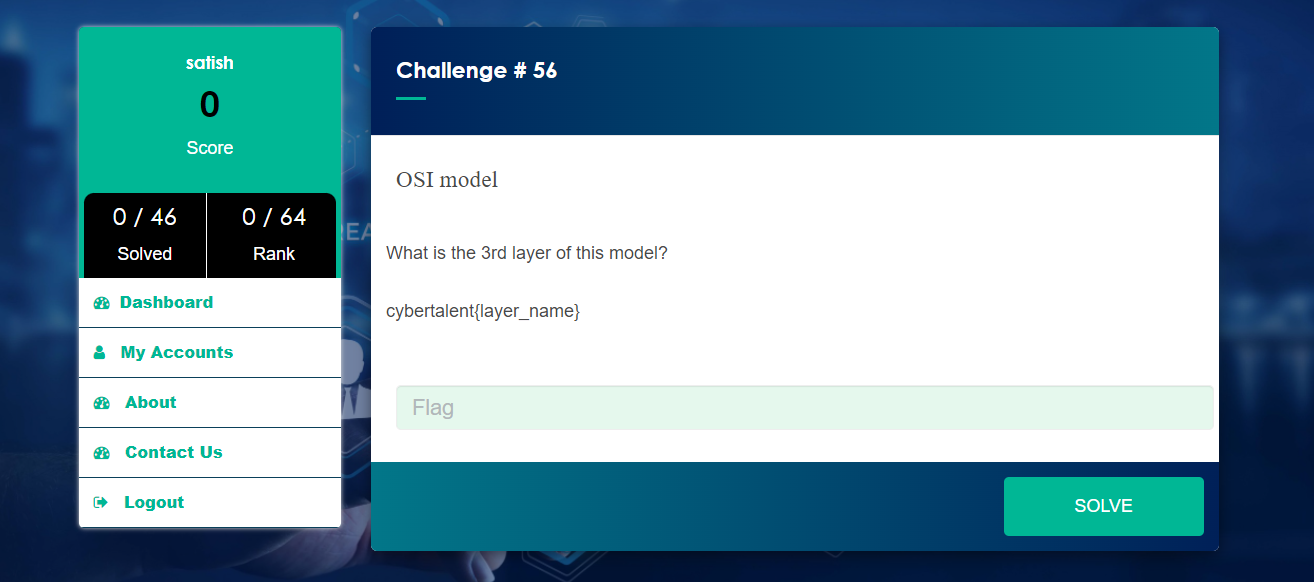
- OSI model
- Telnet
- WHOIS-1
- FTP
- linux_privesc_1
- m4tr1x
- cms_ownage_1
- cms_ownage_2
- compromise-1
- post-exploit-win
- Mr Worldwide
- MS Windows
- Unix-1
- Unix-2
- Broken Windows
- compromise-2
- Ez Pz
- Bank Heist
- Free lunch!
- osint-1
- osint-2
Cyber CTF Lab
×